Recently I was reminiscing with a customer at RB’s Computer Service about the good old days. His uncle grew up on a farm and got his driver’s license when he was 14 years old. According to this customer, all his uncle had to do was to go to the DMV, his dad vouched for him, attesting he was trained to drive on the farm, and it was needed to help with farm work. The story made me think about the evolution of computers, and the web in general. Without formal driver’s training, I suspect my customer’s uncle was not a very good driver. Likewise, most people use their computers and get online at home and at the office with little or no training. As a result, I wonder how many people have made rolling stops into a near miss with a hacker or collided with one because of bad security habits? In this month’s blog we’ll explore some good cybersecurity habits you can incorporate when using your computer and browsing the web.
Good Computer Security Habits
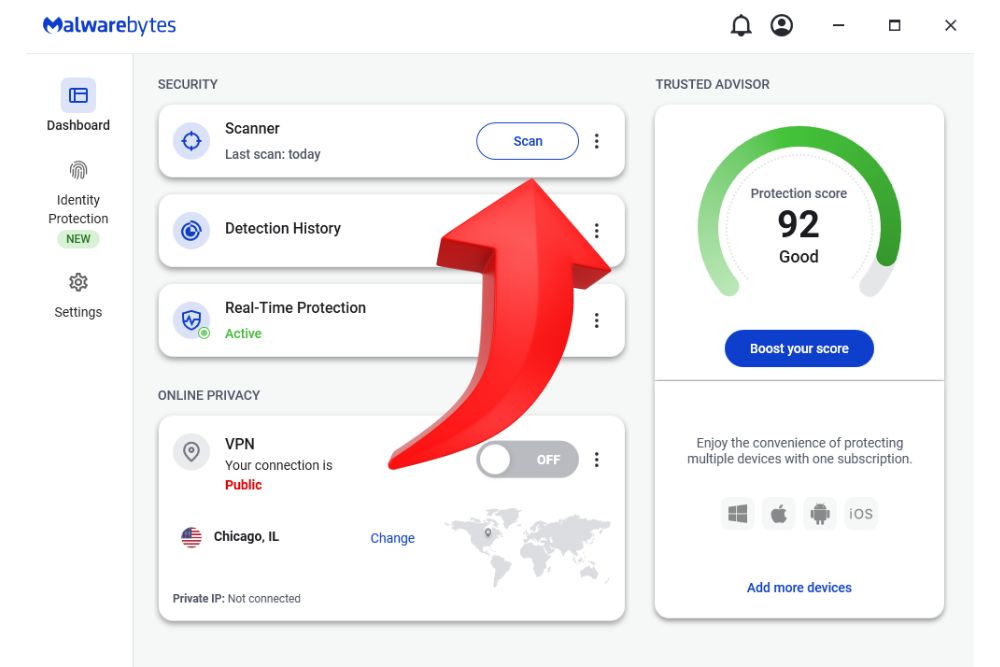 A few months back we helped a customer recover his files and access his network after he was hacked. All his passwords were his daughter’s first name plus the year she was born; “Julie2001.” Up until the hack, he was proud of his minimalistic approach to cybersecurity. The first good habit we recommend is to update your password and do it periodically. If it doesn’t look like this, jJd$wnDHg^NNbE@WSX96CaMY, it probably is not a strong one. In addition to updating passwords, consider:
A few months back we helped a customer recover his files and access his network after he was hacked. All his passwords were his daughter’s first name plus the year she was born; “Julie2001.” Up until the hack, he was proud of his minimalistic approach to cybersecurity. The first good habit we recommend is to update your password and do it periodically. If it doesn’t look like this, jJd$wnDHg^NNbE@WSX96CaMY, it probably is not a strong one. In addition to updating passwords, consider:
- Downloading and installing a password manager app on all of your devices if strong passwords are too hard to remember.
- Strong passwords should be at least 20 characters and store your passkeys in a “vault” or app. A passkey is a digital credential that allows users to sign in to apps and websites using the same steps they use to unlock their device (biometrics, PIN, or pattern), replacing the need for passwords and enhancing security and convenience.
- Install antivirus software on all your internet-connected devices.
- Check to make sure your antivirus software is running.
- Monitor your credit report and investigate any suspicious activity immediately.
Good Digital Housekeeping Habits
- Install operating system patches or updates. Most people use Microsoft. Microsoft often
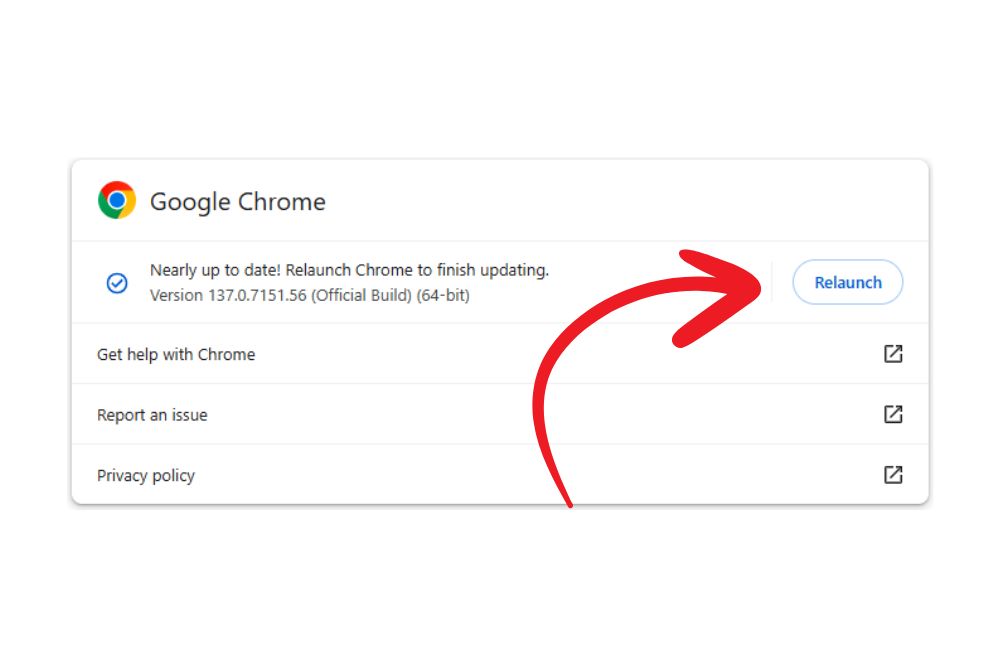 updates automatically as the default. But you can check too. For Windows 11 users, go to Start > Settings > Windows Update and click "Check for updates".
updates automatically as the default. But you can check too. For Windows 11 users, go to Start > Settings > Windows Update and click "Check for updates". - Update your web browser. If you use Google Chrome, Google Chrome is consistent in reminding users to do this.
- Update your antivirus software. McAfee, Malwarebytes, and Norton offer updates automatically as the default. But you can click to check yourself.
- Back up your data to an offline source and store it securely. If you need help with backups, don’t hesitate to contact RB’s Computer Service at 763-441-3884 or email us at help@rbsmn.com.
- Clear the browser cache on all of your devices.
- Browse the library on your mobile devices and delete out-of-date or unused apps.
Good Web Browsing Habits
 A few months ago, I wrote a blog about hackers and scammers using AI to impersonate people’s voices, AI Voice Scams Dad Out of 25K. These AI driven scams have the potential to trick anyone. The best thing is to be suspicious of unsolicited phone calls, and don’t open files attached to emails and messages from senders you don't recognize. Some other good habits are:
A few months ago, I wrote a blog about hackers and scammers using AI to impersonate people’s voices, AI Voice Scams Dad Out of 25K. These AI driven scams have the potential to trick anyone. The best thing is to be suspicious of unsolicited phone calls, and don’t open files attached to emails and messages from senders you don't recognize. Some other good habits are:
- Don't click on links from senders you don't recognize.
- Don't send money online to anyone you've never met in person.
- Don't overshare news about your family, job, vacation, or other personal life events on public social media sites.
- Always enable a form of multi-factor authentication for your online accounts.
- Always turn on multi-factor authentication for your online accounts.
- Always protect your devices with a passcode or biometric authentication.
Bottom Line
 The cybersecurity habits outlined above could help you avoid colliding with a hacker or scammer. Habits take some effort and discipline to be effective. For example, for my car maintenance, I routinely check the oil and bring it in for an oil change every 3000 miles or so. Like computer users, I didn’t get trained to do this but developed the habit. It is the same with good cybersecurity habits. Of the good habits listed above, for most of the items, except computer and network backups, a novice computer user can develop a routine to do them. But if you don’t have the time, or need help with anything, RB’s Computer Service offers uncomplicated and affordable Managed IT Service Agreements to help protect you. Contact us today at 763-441-3884 or email us at help@rbsmn.com. In addition to cybersecurity, RB’s Computer Service provides ransomware strategies and sells the best commercial-grade firewall routers, best laptop computers, best desktop computers, business computers, computer parts, and computer monitors. We also provide computer repair, iPhone and smartphone repair, and tablet repairs to customers and clients throughout central Minnesota and St. Cloud.
The cybersecurity habits outlined above could help you avoid colliding with a hacker or scammer. Habits take some effort and discipline to be effective. For example, for my car maintenance, I routinely check the oil and bring it in for an oil change every 3000 miles or so. Like computer users, I didn’t get trained to do this but developed the habit. It is the same with good cybersecurity habits. Of the good habits listed above, for most of the items, except computer and network backups, a novice computer user can develop a routine to do them. But if you don’t have the time, or need help with anything, RB’s Computer Service offers uncomplicated and affordable Managed IT Service Agreements to help protect you. Contact us today at 763-441-3884 or email us at help@rbsmn.com. In addition to cybersecurity, RB’s Computer Service provides ransomware strategies and sells the best commercial-grade firewall routers, best laptop computers, best desktop computers, business computers, computer parts, and computer monitors. We also provide computer repair, iPhone and smartphone repair, and tablet repairs to customers and clients throughout central Minnesota and St. Cloud.
References
The best antivirus software in 2025: top picks ranked and reviewed for PC
https://www.techradar.com/best/best-antivirus
Cybersecurity for Small Business
https://www.ftc.gov/business-guidance/small-businesses/cybersecurity
Cybersecurity Checklist: Follow These Simple Steps to Break Bad Habits
https://www.pcmag.com/explainers/ramp-up-your-cybersecurity-with-pcmags-online-safety-checklist
