According to Verizon, 30% of phishing messages get opened by targeted users. In 2018, experts predicted phishing scams would cause damages exceeding $9 billion. This is a huge increase from the $5.3 billion in damages that occurred in 2017. (ZetaSky, Chapter 1: Five types of phishing attack that can harm your business, November 1st, 2019, https://www.zetasky.com/2019/11/five-types-of-phishing-attack-that-can-harm-your-business/). At the same time,  website spoofing doubled in 2018, resulting in $1.3 billion in losses (DarkReading®, Dr. Salvatore Stolfo, Rethinking Website Spoofing Mitigation, August 7th, 2019, https://www.zdnet.com/article/ransomware-should-you-pay-up). I’d venture to say that most people have been targeted in one way or another over the last few years. Victims of phishing scams are not just business owners, consumers are also prey for this scam. Unfortunately, many people don’t know what a phishing scam is, nor know how they can help protect themselves. In this blog, I’ll briefly describe two common types of phishing scams: “website forgery” and “clone phishing” and ways you can protect yourself from becoming a victim.
website spoofing doubled in 2018, resulting in $1.3 billion in losses (DarkReading®, Dr. Salvatore Stolfo, Rethinking Website Spoofing Mitigation, August 7th, 2019, https://www.zdnet.com/article/ransomware-should-you-pay-up). I’d venture to say that most people have been targeted in one way or another over the last few years. Victims of phishing scams are not just business owners, consumers are also prey for this scam. Unfortunately, many people don’t know what a phishing scam is, nor know how they can help protect themselves. In this blog, I’ll briefly describe two common types of phishing scams: “website forgery” and “clone phishing” and ways you can protect yourself from becoming a victim.
What are Phishing Scams?
Phishing is a fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details by disguising oneself as a trustworthy entity in an electronic communication. Typically carried out by email spoofing or instant messaging, it often directs users to enter personal information at a fake website that matches the look and feel of the legitimate site. https://en.wikipedia.org/wiki/Phishing
What is Website Forgery?
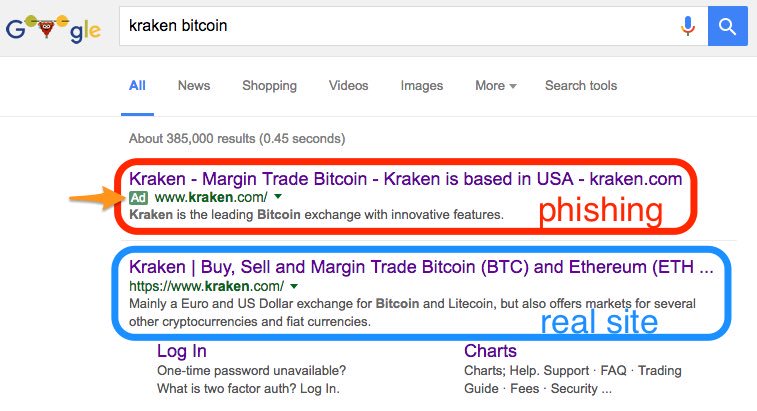
Some phishing scams use JavaScript commands in order to alter the address bar of the website they lead to. This is done either by placing a picture of a legitimate URL over the address bar or by closing the original bar and opening up a new one with the legitimate URL.
An attacker can also potentially use flaws in a trusted website's own scripts against the victim. These types of attacks (known as cross-site scripting) are particularly problematic because they direct the user to sign-in at their bank or servicer's own web page, where everything from the web address to the security certificates appears correct. In reality, the link to the website is crafted to carry out the attack, making it very difficult to spot without prior special knowledge. Such a flaw was used in 2006 against PayPal. https://en.wikipedia.org/wiki/Phishing
What is Clone Phishing?
Clone phishing is a type of phishing attack whereby a legitimate and previously delivered email, containing an attachment or link, has had its content and recipient address taken and used to create an almost identical or cloned email. The attachment or link within the email is replaced with a malicious version and then sent from an email address spoofed to appear to come from the original sender. It may claim to be a resend of the original or an updated
version to the original. Typically this requires either the sender or recipient to have been previously hacked for the malicious third party to obtain the legitimate email. https://en.wikipedia.org/wiki/Phishing
How to Prevent Website Forgery and Clone Phishing?
RB’s Computer Service has been educating businesses and consumers doing business with us helping them prevent phishing scams for over 10 years. It is nearly impossible to provide a-catch-all punch list in one blog. If you suspect that you may have been a victim of phishing and need repairs you may contact us for repairs. Nevertheless, below are 5 ideas to consider that can help protect yourself or your business.
• Use a Web browser with anti-phishing detection. Internet Explorer, Mozilla Firefox, Web browsers have free add-ons (or “plug-ins”) that can help you detect phishing sites. Google Chrome can now warn you in real-time if you're getting phished, see https://www.cnet.com/news/google-chrome-can-now-warn-you-in-real-time-if-youre-getting-phished/
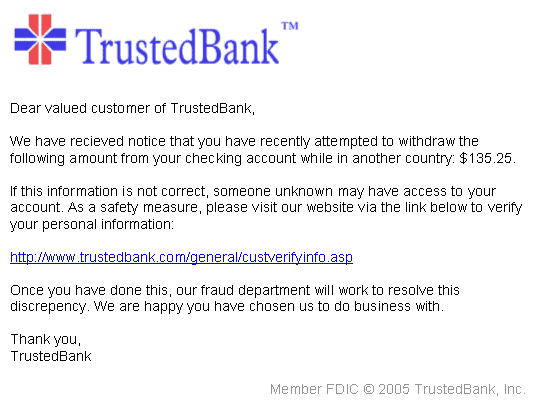
• Be leery of pop-ups. Be careful if you’re sent to a website that immediately displays a pop-up window asking you to enter your username and password. Phishing scams may direct you to a legitimate website and then use a pop-up to gain your account information (Techies Journal, Prasad Paul, Website spoofing: How to prevent a spoofing attack?, April 14th, 2017, http://www.techiesjournal.com/website-spoofing-prevent-spoofing-attack/).
• To defend against website spoofing, make sure you access a website via SSL (Security Certificate: You can tell by the lockbox icon in front of the website URL/Domain Name or https://). Non-SSL (Security Certificate) websites provide a multitude of spoofing opportunities for hackers, so if you’re looking to avoid that fate, ensure that the website has an SSL (Comparitech, Tim Keary, A Guide to Spoofing Attacks and How to Prevent Them, November 21, 2018, https://www.comparitech.com/net-admin/spoofing-attacks-guide/).
• Deploy anti-virus software on your devices. Using anti-virus software on your devices will make sure that they can deal with any malicious software that has been planted.
• Install firewalls on your network or use a commercial-grade router. A firewall will help to keep unwanted intruders out and ensure your network stays protected. RB’s Computer Service can help set yours up. See blog: https://rbsmn.com/switching-to-a-commercial-grade-router.
• Start using VPNs. A VPN or a Virtual Private Network encrypts data so that it cannot be read by an external party. RB’s Computer Service can help set yours up. See blog: https://rbsmn.com/integrate-vpn-for-personal-or-business-use-today.
For help protecting yourself or your business from phishing scams, or if you have questions, contact us today via phone 763-441-3884 or email at help@rbsmn.com. In addition to providing computer and data security protection and solutions, RB’s Computer Service offers Ransomware strategies. We also sell the best commercial-grade firewall routers, best laptop computers, best desktop computers, business computers, computer parts, and computer monitors. We provide services for computer repair, iPhone and smartphone repair and tablet repairs to customers and clients throughout central Minnesota and St. Cloud.