 Phishing scams are constantly evolving to adopt new forms and techniques. Businesses of all sizes need to take steps to protect themselves. The average 10,000-employee company spends $3.7 million a year dealing with phishing attacks (Maria Korolov, CSO from IDG, Phishing is a $3.7-million annual cost for average large company, August 26th, 2015 https://www.csoonline.com/article/2975807/cyber-attacks-espionage/phishing-is-a-37-million-annual-cost-for-average-large-company.html). For some small business owners, phishing scams seem like something only the “big guys” have to deal
Phishing scams are constantly evolving to adopt new forms and techniques. Businesses of all sizes need to take steps to protect themselves. The average 10,000-employee company spends $3.7 million a year dealing with phishing attacks (Maria Korolov, CSO from IDG, Phishing is a $3.7-million annual cost for average large company, August 26th, 2015 https://www.csoonline.com/article/2975807/cyber-attacks-espionage/phishing-is-a-37-million-annual-cost-for-average-large-company.html). For some small business owners, phishing scams seem like something only the “big guys” have to deal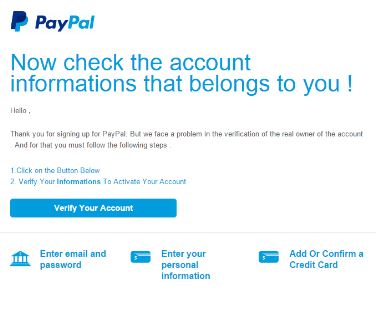 with, but that assumption is far from reality. For example, in July of 2015 phishing hackers created a website to mimic Google Drive to harvest user credentials when they login. Not only did Google unknowingly host that fake login page, but a Google SSL certificate also protected the page with a secure connection (David Bisson, tripwire.com, 6 Common Phishing Attacks and How to Protect Against Them, June 5th 2016, https://www.tripwire.com/state-of-security/security-awareness/6-common-phishing-attacks-and-how-to-protect-against-them/). As mentioned above, phishing scams are constantly evolving and numerous. For the sake of this article I’ll touch on 3 common examples, define what phishing scams are for those new to the subject, and wrap up with several ways business owners can protect themselves and how RB’s Computer Service can help in that effort. What is a Phishing Scam? According to the Federal Trade Commission, “phishing is when a scammer uses fraudulent emails or texts, or copycat websites to get you to share valuable personal information – such as account numbers, Social Security numbers, or your login IDs and passwords. Scammers use your information to steal your money or your identity or both https://www.consumer.ftc.gov/articles/0003-phishing. Three Types of Phishing
with, but that assumption is far from reality. For example, in July of 2015 phishing hackers created a website to mimic Google Drive to harvest user credentials when they login. Not only did Google unknowingly host that fake login page, but a Google SSL certificate also protected the page with a secure connection (David Bisson, tripwire.com, 6 Common Phishing Attacks and How to Protect Against Them, June 5th 2016, https://www.tripwire.com/state-of-security/security-awareness/6-common-phishing-attacks-and-how-to-protect-against-them/). As mentioned above, phishing scams are constantly evolving and numerous. For the sake of this article I’ll touch on 3 common examples, define what phishing scams are for those new to the subject, and wrap up with several ways business owners can protect themselves and how RB’s Computer Service can help in that effort. What is a Phishing Scam? According to the Federal Trade Commission, “phishing is when a scammer uses fraudulent emails or texts, or copycat websites to get you to share valuable personal information – such as account numbers, Social Security numbers, or your login IDs and passwords. Scammers use your information to steal your money or your identity or both https://www.consumer.ftc.gov/articles/0003-phishing. Three Types of Phishing
- Deceptive Phishing. In this type of attack, a scammer sends an email impersonating a legitimate company and attempts to steal your personal information or login credentials. The emails often use threats and a sense of urgency to frighten users into doing what the scammer is asking for, like to click on a link in order to fix a discrepancy with their account. When they click on the link, they are lead to a fake login page that collects a user’s login credentials and delivers them to the fraudster (see PayPal example below). Another form or this is called “spear phishing.” This type of email goes a step further with a customized salutation with the target’s name, position, company, work phone number and other information in an attempt to trick the recipient (David Bisson, tripwire.com, 6 Common Phishing Attacks and How to Protect Against Them, June 5th 2016, https://www.tripwire.com/state-of-security/security-awareness/6-common-phishing-attacks-and-how-to-protect-against-them/).
- CEO Fraud. Deceptive & spear phishers can target anyone in an organization, such as the President, CEO and top executives. Once a scammer gets access to the executives email credentials, they impersonate him or her to authorize fraudulent wire transfers to a financial institution of their choice (David Bisson, tripwire.com, 6 Common Phishing Attacks and How to Protect Against Them, June 5th 2016, https://www.tripwire.com/state-of-security/security-awareness/6-common-phishing-attacks-and-how-to-protect-against-them/).
- Pharming, Dropbox and Google Drive. A “pharmer” targets a DNS server and changes the IP address associated with an alphabetical website name. That means an attacker can redirect users to a malicious website of their choice even if the victims entered in the correct website name. Dropbox and Google Drive are 2 examples of this. Scammers sent people to a fake site to login to collect their credentials (David Bisson, tripwire.com, 6 Common Phishing Attacks and How to Protect Against Them, June 5th 2016, https://www.tripwire.com/state-of-security/security-awareness/6-common-phishing-attacks-and-how-to-protect-against-them/).
Way to Prevent Phishing  The three types of phishing scams highlighted above are only some of the many forms scammers use. There are a seemingly endless number of variations. As you can see from the PayPal example above, it looks legitimate and almost anyone could fall for it. Some of the ways you can protect yourself include:
The three types of phishing scams highlighted above are only some of the many forms scammers use. There are a seemingly endless number of variations. As you can see from the PayPal example above, it looks legitimate and almost anyone could fall for it. Some of the ways you can protect yourself include:
- Protect your computer with a firewall, spam filters, anti-virus and anti-spyware software. RB’s Computer Service can help you with this.
- Email users should consider implementing two-step verification (2SV) on their accounts. And when prompted by third parties with this option, like Facebook, you should opt-in to their two-step verification.
- Never enter personal information in a pop-up screen.
- Beware of links in emails that ask for personal information.
- Never email personal or financial information, even if you are close with the recipient.
- Do not click on links, download files or open attachments in emails from unknown senders.
- Communicate personal information only via phone or secure web sites.
- The boss should encourage employees to enter in login credentials only on HTTPS-protected sites.
- Consider a VPN, RB’s Computer Service can help with this too. See our blog: https://rbsmn.com/2018/02/07/integrate-vpn-for-personal-or-business-use-today
Without knowing the readers needs and network, it is almost impossible to pinpoint exactly what you might need to protect yourself against a phishing scam. Some of it is common sense, and some of it requires some help. Either way, this blog can serve as a road map to take action today. For help with your business, contact us via phone or email: 763-441-3884, or help@rbsmn.com. In addition phishing prevention, we also offer ransomware strategies, and sell the best commercial grade firewall routers, best laptop computers, best desktop computers, business computers, computer parts and computer monitors. We also provide managed IT services, computer repair, iPhone and smartphone repair and tablet repairs to customers and clients throughout central Minnesota and St. Cloud.
