
Many of RB’s Computer Service customers began using a computer in the 1990’s. Back then, most malware targeted Microsoft users and was primarily designed to infect and compromise its functionality. In 1991, Norton Anti-Virus Software came out. To sidestep malware throughout the decade, computer users could install and use Norton with confidence they were safe. Unfortunately, malware has evolved, and today anti-virus software is not enough to protect your computer, privacy, or computer network. Some Gen X computer users bring in their infected computers to RB’s Computer Service and they are dumbfounded on what happened. Many report they were running the latest version of Norton or some other anti-virus software. While this is a great first line of defense, anti-virus software is not enough to protect against malware today. In this blog, we’ll explore what malware used to look like in the 1990s versus today and highlight some cybersecurity steps you can take to protect against it today.
Software came out. To sidestep malware throughout the decade, computer users could install and use Norton with confidence they were safe. Unfortunately, malware has evolved, and today anti-virus software is not enough to protect your computer, privacy, or computer network. Some Gen X computer users bring in their infected computers to RB’s Computer Service and they are dumbfounded on what happened. Many report they were running the latest version of Norton or some other anti-virus software. While this is a great first line of defense, anti-virus software is not enough to protect against malware today. In this blog, we’ll explore what malware used to look like in the 1990s versus today and highlight some cybersecurity steps you can take to protect against it today.
Malware 1971 thru the 1990s
The Creeper
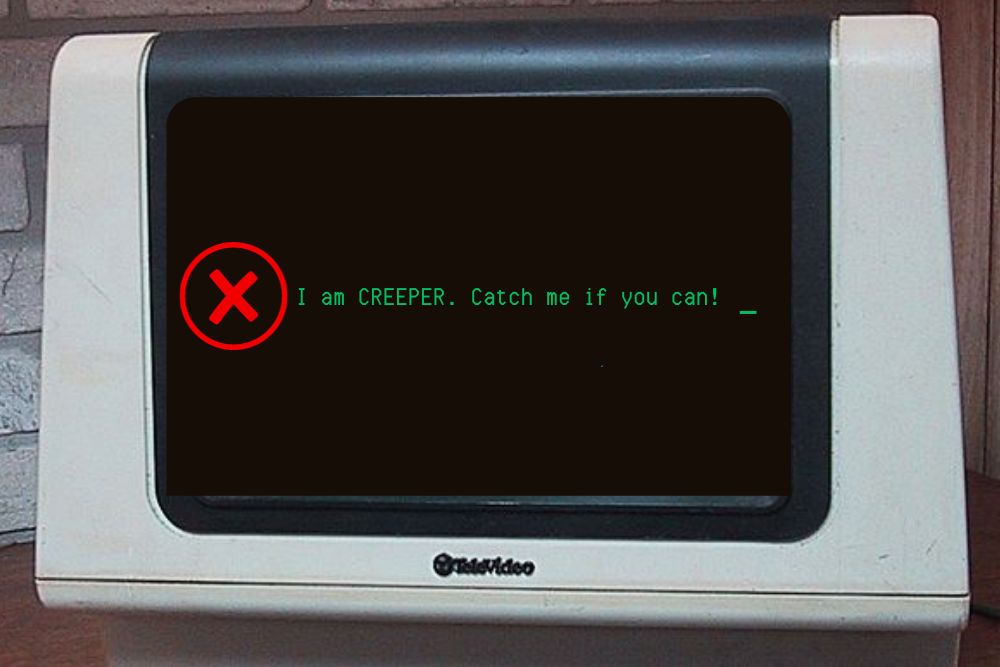 The first computer virus appeared in 1971 and was called “The Creeper.” It was a message displayed on connected teletype computer screens and read: “I’m the creeper, catch me if you can!” But The Creeper wasn’t malware like we associate with today’s computer viruses. It simply displayed its enigmatic message. It didn’t encrypt files, demand a ransom, destroy data, steal Social Security numbers, or render centrifuges inoperable. It only displayed its taunting challenge. Its creator had simply wanted to create an experimental, self-duplicating program to illustrate that it was possible.
The first computer virus appeared in 1971 and was called “The Creeper.” It was a message displayed on connected teletype computer screens and read: “I’m the creeper, catch me if you can!” But The Creeper wasn’t malware like we associate with today’s computer viruses. It simply displayed its enigmatic message. It didn’t encrypt files, demand a ransom, destroy data, steal Social Security numbers, or render centrifuges inoperable. It only displayed its taunting challenge. Its creator had simply wanted to create an experimental, self-duplicating program to illustrate that it was possible.
The 1990s
In the 1990s, malware was primarily designed to infect and compromise the operation of computer systems. Many viruses of this era were created to spread rapidly, often through infected floppy disks, email attachments, or network connections. These viruses aimed to disrupt the normal functioning of the target system, causing data loss and operational problems. Overall, computer viruses in the 1990s had a range of objectives, from self-replication and system disruption to data theft and control.
Today’s Malware
 Malware in the 1990s was more like a mischievous pest, but today malware can lead to financial ruin, identity theft, shutdowns of business operations, and dangerous consequences for individuals, businesses, and organizations that fall victim to it. Some of the goals and tactics of modern malware include:
Malware in the 1990s was more like a mischievous pest, but today malware can lead to financial ruin, identity theft, shutdowns of business operations, and dangerous consequences for individuals, businesses, and organizations that fall victim to it. Some of the goals and tactics of modern malware include:
Financial Gain
One of the primary motivations for contemporary malware is financial profit. This includes banking trojans that steal login credentials and financial information, ransomware that encrypts data and demands a ransom for decryption keys, and cryptocurrency miners that hijack computing resources to mine digital currencies. The aim is to extort money from individuals, businesses, or organizations. For more information on ransomware, please see RB’s blog “3 Types of Ransomware and Ways to Avoid Becoming a Victim.”
Data Theft and Espionage
State-sponsored actors and cybercriminals deploy sophisticated malware to steal sensitive information, trade secrets, or government intelligence. Advanced Persistent Threats (APTs) use custom-made malware to maintain persistent access to a target network, enabling long-term espionage. For more information on this, please see RB’s blog “What is “Killware” and Should it Concern You?”
Social Engineering and Phishing
Malware is commonly distributed via phishing emails, where the goal is to trick individuals into opening malicious attachments or clicking on malicious links. Social engineering is used to manipulate users into taking actions that benefit the attacker. For more information on email phishing, please see RB’s blog “Phishing Scam Prevention 101.”
Information Warfare and Disinformation
Some malware is designed for political or ideological purposes, engaging in information warfare or disinformation campaigns. This might involve spreading fake news or interfering with critical infrastructure. For more information on ransomware, please see RB’s blog “Sidestep Social Media Scams in 2022.”
Today You Need More than Norton Anti-Virus Software
 If your first and last line of defense against modern malware is Norton Anti-Virus software, it is time to integrate additional cybersecurity steps to protect yourself, your business, or your organization. If you need help, RB’s Computer Service would love to assist you. Simply contact us today via email at help@rbsmn.com or call us at 763-441-3884 for a no-obligation consultation. Some of the cybersecurity areas we’ll explore include:
If your first and last line of defense against modern malware is Norton Anti-Virus software, it is time to integrate additional cybersecurity steps to protect yourself, your business, or your organization. If you need help, RB’s Computer Service would love to assist you. Simply contact us today via email at help@rbsmn.com or call us at 763-441-3884 for a no-obligation consultation. Some of the cybersecurity areas we’ll explore include:
• Password protection. Learn More.
• Encrypted email. Learn More.
• Consider using a VPN. Learn More.
• Commercial Grade Routers. Learn More.
• Is your data backed up? Learn More.
Bottom Line
 Malware is not a mischievous pest as in the 1990s. Today malware can lead to financial ruin, identity theft, shutdowns of business operations, and dangerous consequences for individuals, businesses, and organizations that fall victim to it. To protect yourself, your business, or your organization, you need more than anti-virus software. RB’s Computer Service can help you determine a cybersecurity plan that will provide the best protection and make sense. Don’t hesitate to contact RB’s Computer Service today via email at help@rbsmn.com or call us at 763-441-3884 for a no-obligation consultation. In addition to cybersecurity solutions, RB’s Computer Service offers very affordable Managed IT Service Agreements to ensure your computers and computer networks work securely, and smoothly and do what you need them to do. We sell the best commercial-grade firewall routers, best laptop computers, best desktop computers, business computers, computer parts, and computer monitors. For iPhone, smartphone repair, and tablet repairs, do not hesitate to contact us.
Malware is not a mischievous pest as in the 1990s. Today malware can lead to financial ruin, identity theft, shutdowns of business operations, and dangerous consequences for individuals, businesses, and organizations that fall victim to it. To protect yourself, your business, or your organization, you need more than anti-virus software. RB’s Computer Service can help you determine a cybersecurity plan that will provide the best protection and make sense. Don’t hesitate to contact RB’s Computer Service today via email at help@rbsmn.com or call us at 763-441-3884 for a no-obligation consultation. In addition to cybersecurity solutions, RB’s Computer Service offers very affordable Managed IT Service Agreements to ensure your computers and computer networks work securely, and smoothly and do what you need them to do. We sell the best commercial-grade firewall routers, best laptop computers, best desktop computers, business computers, computer parts, and computer monitors. For iPhone, smartphone repair, and tablet repairs, do not hesitate to contact us.
References
Creeper: The World’s First Computer Virus
https://www.exabeam.com/information-security/creeper-computer-virus/
A Brief History of Computer Viruses from Mischief to Mayhem
https://www.ceros.com/inspire/originals/computer-virus-history/
A History of Malware: Part Three, 1993-1999
https://resources.infosecinstitute.com/topics/malware-analysis/history-malware-part-three-1993-1999/
What is Malware? Definition, Purpose & Common Protections
https://www.esecurityplanet.com/threats/malware/
